- Technical Paper
- Power Systems
Resource Center

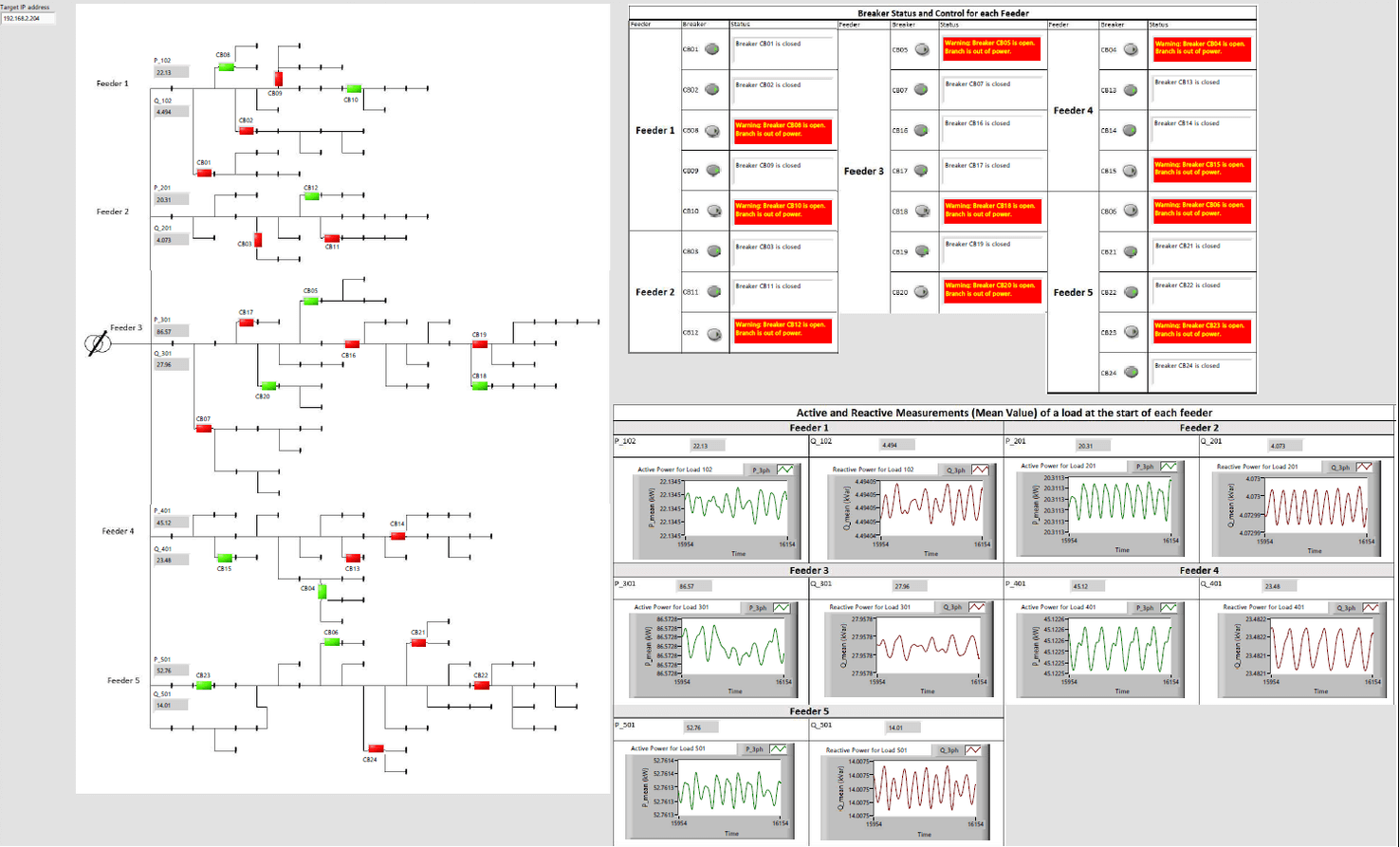
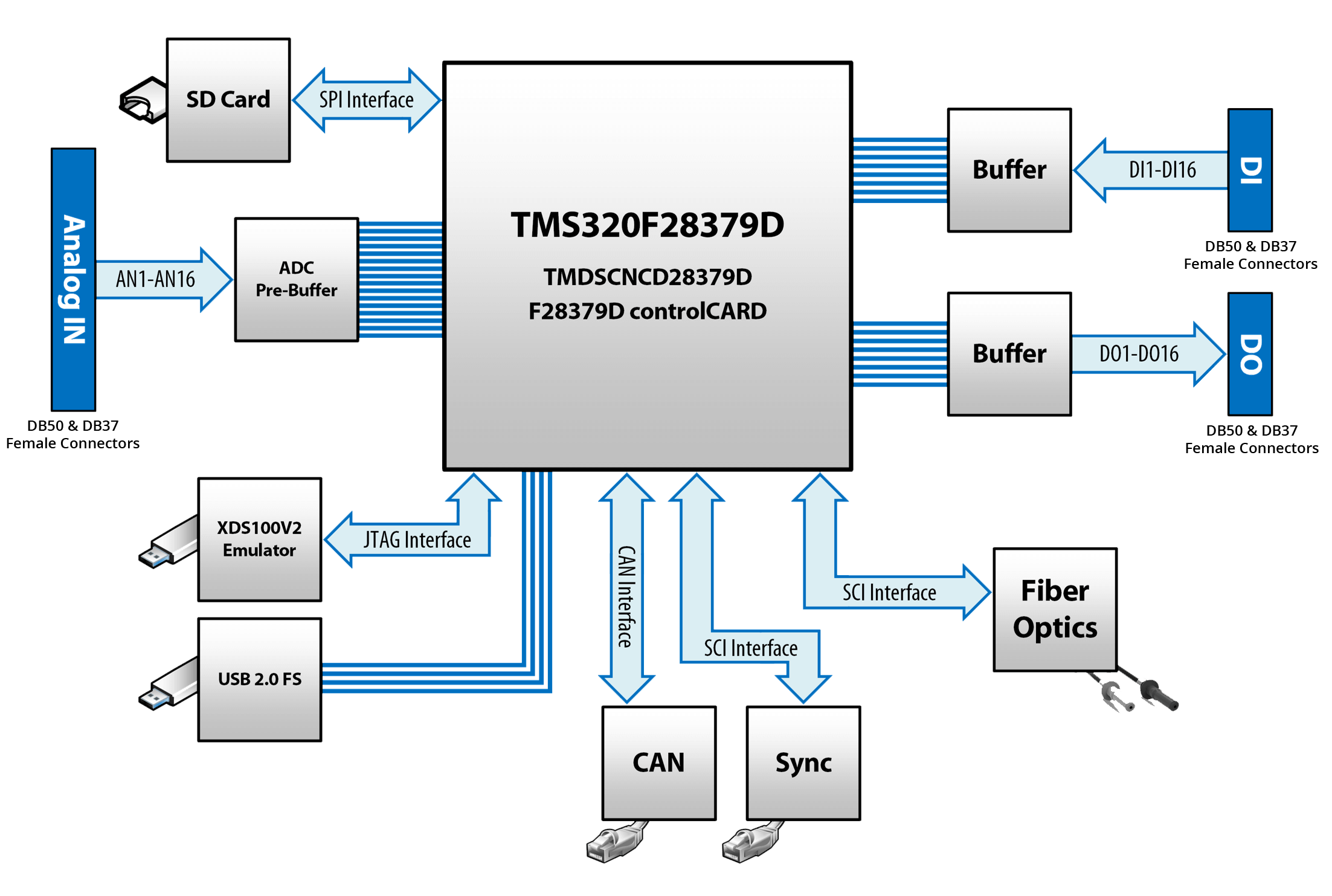
This paper experimentally assesses the impact of time synchronization spoofing attacks (TSSA) on synchrophasor-based Wide-Area Monitoring, Protection and Control applications. Phase Angle Monitoring (PAM), anti-islanding protection and power oscillation damping applications are investigated. TSSA are created using a real-time IRIG-B signal generator and power system models are executed using a real-time simulator with commercial phasor measurement units (PMUs) coupled to them as hardware-in-the-loop. Because PMUs utilize time synchronization signals to compute synchrophasors, an error in the PMUs’ time input introduces a proportional phase error in the voltage or current phase measurements provided by the PMU. The experiments conclude that a phase angle monitoring application will show erroneous power transfers, whereas the anti-islanding protection mal-operates and the damping controller introduces negative damping in the system as a result of the time synchronization error incurred in the PMUs due to TSSA.
The proposed test-bench and TSSA approach can be used to investigate the impact of TSSA on any WAMPAC application and to determine the time synchronization error threshold that can be tolerated by these WAMPAC applications.