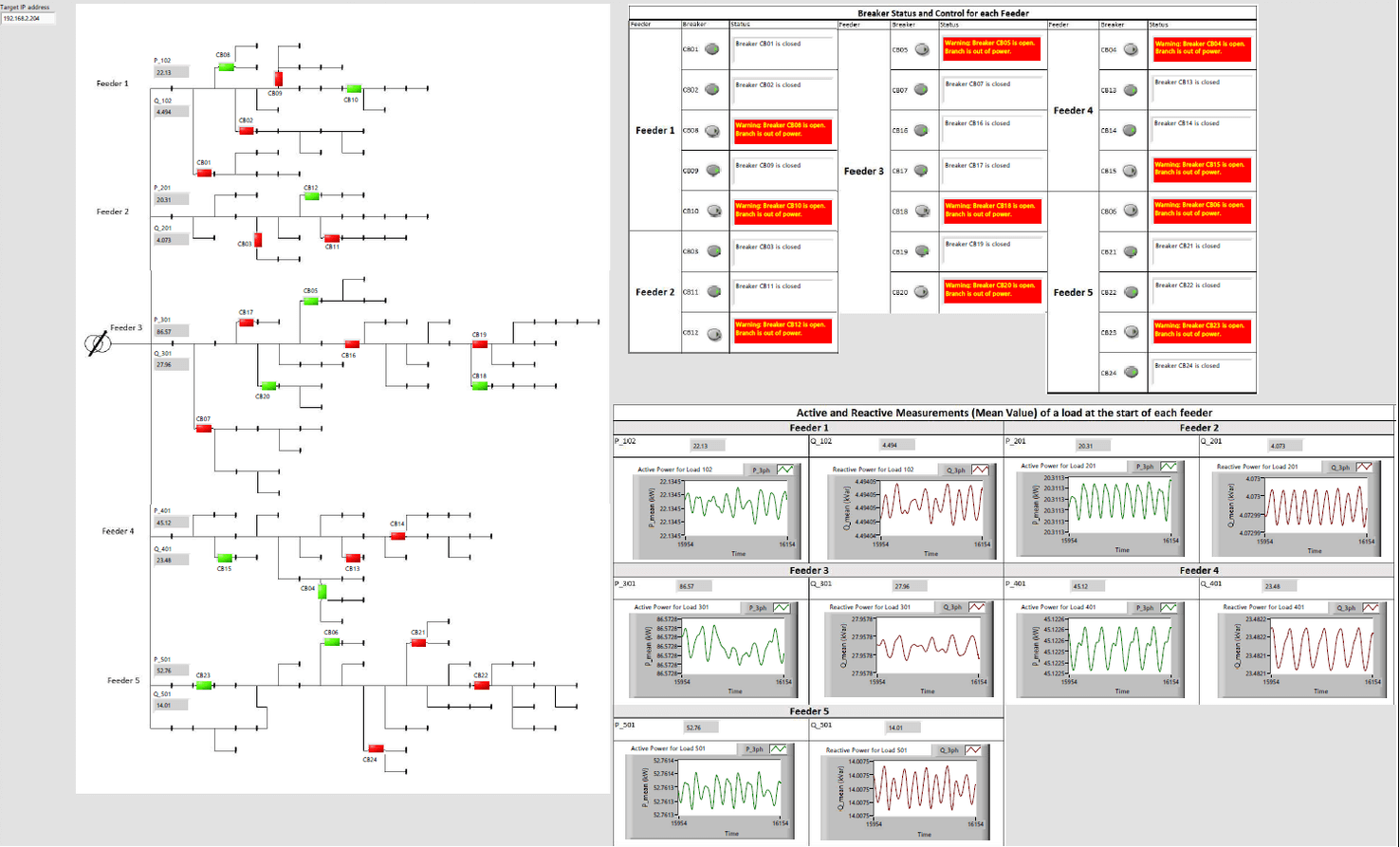
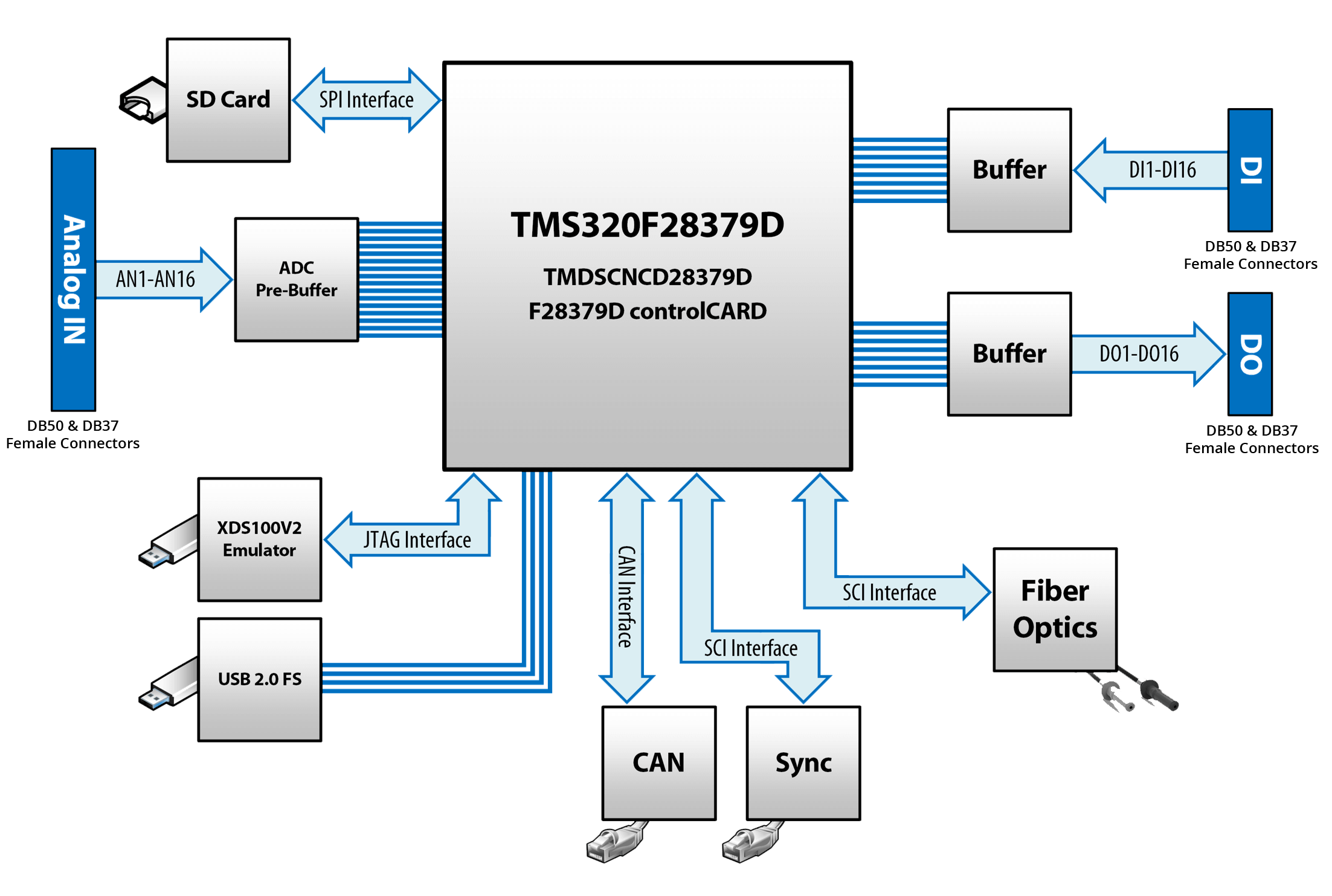
5 Types of Communication Protocols in PLC Systems
Professionals often rely on programmable logic controllers (PLCs) to handle tasks that require precise control, troubleshooting simplicity, and consistent performance. Communication networks serve as the bridge connecting these devices to one another, paving the way for smooth data transfer and reliable automation. Carefully selecting from the types of communication protocols in PLC systems can have a measurable impact on project outcomes, particularly when looking to improve speed to market. Many engineers search for ways to integrate hardware and software effectively, and exploring the types of PLC communication protocols can offer valuable direction when deciding on the best path.
“Communication networks serve as the bridge connecting these devices to one another, paving the way for smooth data transfer and reliable automation.”
Engineers frequently consider factors such as distance coverage, network topology, and cost efficiency before adopting a specific communication standard. Robust interfacing can allow controllers to exchange critical signals, alarms, and configuration data without complications. Coordinating industrial processes in manufacturing, energy generation, or discrete automation grows more seamless when communication standards align with project goals. Many hardware developers also focus on backward compatibility, making it simpler to update older systems without sacrificing stability or performance.
1. Serial Communication Protocols
Modbus RTU (Master/Slave)
Modbus RTU in a master/slave setup uses compact binary messaging for reliable communication between controllers and field devices. The master sends a query, and each slave responds in a structured cycle. This direct approach supports predictable timing, low overhead, and effective monitoring of remote systems. Many industrial projects use Modbus RTU for its clarity, especially when consistent polling and centralized control are essential.
DNP3 Master / DNP3 Slave
DNP3 supports secure, event-based communication between master and slave devices in utility systems and distributed control networks. Masters receive time-stamped updates from slaves only when a meaningful change occurs, reducing bandwidth usage. Its layered structure includes authentication and data integrity checks, which help protect infrastructure. DNP3 is commonly used in electrical grid control, water treatment, and other applications where high reliability is required.
CAN/CAN-FD/CANopen
CAN-based protocols deliver fast, structured data exchange between devices across a shared bus. Standard CAN handles short, fixed-length frames, while CAN-FD extends the payload size for higher efficiency. CANopen builds on this by adding device profiles and network management features tailored for motion control and automation. These protocols are widely used in transportation, robotics, and manufacturing systems that require robust communication and simplified diagnostics.
DF1
DF1 is often linked to certain controller families that demand synchronous data exchange through a full-duplex or half-duplex connection. This approach fosters two-way communication and ensures that message integrity checks are implemented on each frame. The standard encapsulates instructions that enable reading and writing PLC memory, addressing direct I/O control, and resetting error states. Many integrators appreciate DF1 for its adaptability in legacy systems where future upgrades might extend controller lifespans.
HostLink
HostLink targets simple data communication between devices and PLCs, employing a command-response format to organize messaging. This standard typically leverages ASCII-coded data for improved human readability during troubleshooting. Point-to-point wiring structures can keep upfront installation costs low while maximizing stability for smaller projects. Engineers focused on quick system expansions sometimes integrate HostLink for compatibility with older platforms where direct memory mapping remains a vital requirement.
Optomux
Optomux follows a similar master-slave approach but can accommodate multiple I/O modules in a daisy chain. Each module is assigned a unique address, ensuring data exchange remains orderly and preventing collisions. Certain implementations highlight the minimal overhead of the Optomux protocol, improving speed across limited communication lines. This can be important for processes that rely on frequent scanning of analog and digital signals to maintain product quality and throughput goals.
Interbus
Interbus uses a ring topology, passing data through each node in a sequential manner to keep all connected devices updated. The continuous nature of the ring can reduce cabling needs while simplifying installation in systems that require multiple sensing points. Embedded diagnostics in some Interbus implementations alert operators to disruptions, encouraging swift intervention and reducing downtime. High-speed performance and reliable data transfer make it a respected option for control networks where real-time accuracy is paramount.
Point to Point (PP)
Point to Point (PP) connections describe the simplest form of a direct link between two devices. This style typically employs serial communication with straightforward wiring, reducing complexity in settings that do not demand multiple nodes. Implementation costs remain low, and troubleshooting becomes manageable since traffic is limited to two devices. Systems that need minimal overhead or specialized setups often turn to PP wiring for targeted control tasks.
2. Ethernet-Based Communication Protocols
Modbus Master / Modbus Slave
Modbus Master and Slave over TCP/IP follows the same request-response model as the serial version, with improved speed and easier addressing. The master initiates communication while each slave responds based on its assigned IP. This method supports multiple sessions and clear routing, making it useful in segmented automation networks. Industrial users often adopt it for integrating older systems with newer controllers.
EtherCAT Master / EtherCAT Slave
EtherCAT Masters send out a continuous Ethernet frame that passes through each Slave node, which inserts and extracts data on the fly. This structure minimizes delays and keeps cycle times low. Slave devices handle synchronization tasks precisely, making EtherCAT suitable for motion control, robotics, and automation lines that require deterministic timing. The protocol supports device diagnostics through standard error detection features.
PROFINET IO-Device
PROFINET IO-Device communication is structured around cyclic data exchange between a controller and a field device. Each IO-Device updates its input and output status through defined intervals. Its real-time capabilities support advanced motion systems and synchronized control tasks. Engineers use it to reduce wiring while maintaining fast signal response and status feedback across production lines.
BACnet
BACnet is used for building automation systems, linking devices such as HVAC controllers, sensors, and lighting modules over IP networks. It relies on standardized object models to represent physical and logical devices, which simplifies configuration. Devices can share system status and accept control instructions across subsystems. BACnet helps centralize control and improve energy usage tracking in large facilities.
OPC UA / DA
OPC UA and DA facilitate secure and reliable communication between PLCs and software applications. DA works over COM/DCOM for real-time data access in Windows-based systems, while UA supports cross-platform connectivity over TCP/IP. UA also includes structured data models, authentication, and encryption. These protocols are widely used for SCADA integration and supervisory systems across manufacturing and utility sectors.
TCP / UDP
TCP and UDP offer foundational transport layers for Ethernet-based data transmission. TCP ensures reliable delivery through acknowledgments and retries, while UDP supports faster, connectionless transfers for time-sensitive signals. These transport methods support custom or lightweight industrial protocols and are frequently used for internal diagnostics, control logic exchange, or HIL simulation where control over timing is critical.
DNP3 Master / DNP3 Slave
DNP3 over Ethernet supports event-driven updates between masters and slaves, often used in substation automation and energy systems. Devices communicate changes as they happen, conserving bandwidth and reducing polling frequency. Timestamping and secure authentication help protect critical data across supervisory and field layers. Ethernet-based DNP3 is preferred where system visibility and operational continuity are essential.
IEC 60870-5-104 Slave
IEC 60870-5-104 is designed for remote control and telemetry in electrical systems. As a slave protocol, it transmits measurement data and device statuses to a central master. This protocol operates over TCP/IP and includes message timestamps, sequence numbering, and redundancy options. It is well-suited for electrical grid operations that need stable, long-distance communication with substations and control centers.
IEC 61850-8-1 MMS, GOOSE, 9-2 Sampled Values
IEC 61850-8-1 supports three key services: MMS for client-server interactions, GOOSE for fast event-driven messaging, and 9-2 Sampled Values for precise, high-speed data from protection relays. These elements run over Ethernet and are used in substation automation systems to meet strict timing and interoperability requirements. The standard supports integration across IEDs, SCADA, and simulation tools with minimal latency.
EtherNet/IP
EtherNet/IP employs an application layer protocol that organizes control-level information over standard Ethernet infrastructure. This strategy allows high-speed communication, making it suitable for processes that require short update cycles. Message prioritization can be configured to ensure real-time I/O data is not delayed, improving operational consistency. Users benefit from wide adoption and straightforward expansion options that can help scale a system as business needs grow.
Automation/Allen-Bradley PLCs
Automation/Allen-Bradley PLCs commonly support an Ethernet-based protocol that streamlines interactions among local and remote I/O modules. Data exchange uses a common industrial protocol (CIP) structure, which handles explicit messaging for configurations and implicit messaging for real-time control. Network administrators can segment traffic for better performance, addressing cost concerns by adding managed switches only where necessary. This approach can be beneficial in achieving stable production processes that rely on flexible topologies or multiple device vendors.
Profinet
Profinet integrates industrial Ethernet with performance optimizations that aim for deterministic control. Engineers often adopt it to unify discrete, process, and motion tasks under a single communication framework. The protocol supports real-time classes for different speed requirements, ensuring high-priority data is delivered first. Network planning may involve specialized switches or cables, yet the resulting reliability can reduce unplanned stops and safeguard operational continuity.
“EtherCAT applies a unique frame processing technique, where nodes extract or insert data on the fly as frames pass through.”
3. Fieldbus Communication Protocols
CAN / CAN-FD / CANopen
CAN-based protocols offer structured data exchange over a shared bus using short, prioritized messages. CAN-FD increases payload capacity and bit rate, while CANopen introduces standardized device profiles and network control for automation tasks. These systems are commonly used in embedded control, mobile equipment, and distributed machine systems where precise signaling and low latency are required. CAN-based networks reduce wiring and offer strong fault tolerance through message-based error handling.
EtherCAT Master / EtherCAT Slave
EtherCAT used as a fieldbus protocol distributes real-time data across connected Slave devices with a single Master managing the frame cycle. Data is processed as it moves through each node, allowing fast exchange without delays from polling. The format supports detailed diagnostics, time synchronization, and reliable control, making it suitable for distributed drive systems and modular machine designs. EtherCAT’s structure simplifies node addressing and reduces transmission overhead.
PROFINET IO-Device
PROFINET used in fieldbus applications connects IO-Devices to controllers through deterministic Ethernet communication. Each device exchanges input and output data in a defined cycle, allowing real-time updates for coordinated control systems. This setup supports modular installations and simplifies cabling by using a standard Ethernet layer. PROFINET systems often include device diagnostics and status flags that support predictive maintenance and reduce troubleshooting time.
Modbus Master / Modbus Slave
Modbus used in a fieldbus configuration provides predictable request-response communication over RS-485 networks. The Master device sends polling instructions to each Slave in turn, allowing structured control over remote I/O and registers. This structure is suitable for smaller systems requiring clear device roles and minimal overhead. Many legacy PLC installations still use Modbus in this format for its simplicity, open structure, and low deployment cost.
Profibus (DP/PA)
Profibus (DP/PA) supports both discrete (DP) and process automation (PA) domains through a master-slave approach. DP targets high-speed data exchange for tasks like discrete I/O scanning, while PA focuses on sensor and actuator integration in process environments. The deterministic response is often valued in continuous production lines where scanning intervals must remain predictable. Integrators can tailor cycle times and diagnostic settings, providing better project scalability even in large plants.
DeviceNet
DeviceNet employs a CAN (Controller Area Network) base but introduces higher-layer functions tailored for industrial automation. Its compact message structure and error detection capabilities enhance reliability in busy production lines. Network topology options include trunk, drop lines, and power over the bus, which helps reduce extra wiring. The accessible hardware often suits applications involving cost-sensitive expansions or smaller networks with scattered I/O points.
ControlNet
ControlNet operates at high speeds and integrates time-critical data exchange with scheduled messaging. The design allows a single medium to handle both I/O updates and peer-to-peer information, simplifying wiring. Each node has a unique address, and information is transferred in deterministic slots, which is useful when cycle times need to be consistent. Many operators pair ControlNet with other protocols to build redundant control structures or meet intricate safety requirements.
ASI (Actuator Sensor Interface)
ASI (Actuator Sensor Interface) uses a two-wire cable for both power and data transfer, reducing installation complexity. The flat topology allows multiple slave devices to connect, typically with a single master in control. Diagnostics often extend to short-circuit monitoring, which helps technicians detect issues faster. The approach aligns with plants seeking cost-effective wiring solutions and simplified device addressing in large sensor arrays.
4. Wireless Communication Protocols
Wireless Communication Protocols involve sending signals over radio waves, often employing standards like Wi-Fi, Bluetooth, or specialized industrial wireless options. Wireless can free equipment from fixed cable paths, opening opportunities to position sensors in areas that might be hazardous or physically unreachable with wiring. Many professionals use security features such as encryption and authentication keys to protect data integrity across the network. This solution helps scale automation projects across expansive areas while minimizing installation overhead and rework.
5. Other Notable Protocols
HART (Highway Addressable Remote Transducer)
HART superimposes a digital signal on the standard 4–20 mA analog loop, providing simultaneous analog and digital data transfer. The digital portion can share additional parameters such as diagnostics or process variables, which can be insightful for optimizing control. A primary benefit involves backward compatibility with legacy analog systems while offering advanced capabilities for asset management. This dual-communication style lowers total cost of ownership, especially if existing analog wiring remains intact.
DF1, Data Highway Plus (DH+)
DF1 and DH+ provide multi-drop links or token-passing mechanisms to link PLCs and other equipment. DF1 can serve as a simpler option using serial channels, whereas DH+ leverages proprietary networking for faster data throughput. Both protocols include error-checking to avoid invalid messages and keep the control scheme responsive. Many industries still depend on these for legacy connectivity, especially when upgrading older installations without overhauling entire networks.
DNP3 (Distributed Network Protocol)
DNP3 handles data transfer between supervisory control and remote devices, emphasizing time stamping and historical event records. Power utilities frequently use it to manage substations and gather feedback for load adjustments. The protocol accommodates slow or noisy links, ensuring reliability in challenging conditions. Some implementations rely on Secure Authentication mechanisms that protect critical infrastructures from unauthorized access.
DirectNet
DirectNet focuses on enabling communication among controllers and operator interfaces. It organizes data into specific memory registers, allowing straightforward read/write access to PLC memory. Certain automation systems benefit from built-in command sets for timed tasks and event triggering, which helps reduce overhead on the main processor. The approach suits engineers who prefer a direct method to coordinate multiple controllers with minimal complexity.
Key Factors Influencing Protocol Selection
Engineers frequently weigh speed requirements, wiring complexity, and hardware compatibility before choosing a communication protocol. Some projects demand extreme reliability or harsh conditions, guiding decision-makers toward robust industrial standards that manage interference. Other scenarios prioritize cost efficiency, where simpler wiring and minimal overhead can expand operations without major capital outlay. Selecting the right protocol often unlocks untapped potential, making it easier to develop control systems over time.
Benefits of Common PLC Communication Protocols
A unified approach is often useful for consistent device interactions and data handling. Many organizations rely on standardized solutions to gain flexibility and streamline expansion. Several protocols foster real-time performance, which can strengthen quality control in production. Selecting a well-supported system can trim downtime risks, leading to quicker return on investment and more predictable outcomes.
- Reduced wiring costs: Consolidated signals often eliminate the need for separate cables, minimizing installation expenses.
- Scalability: Engineers can adapt their networks as requirements shift, adding devices without rewriting significant portions of the control logic.
- Interoperability: Standardized protocols support a broad range of hardware, promoting integration without lengthy vendor negotiations.
- Enhanced diagnostics: Many protocols include advanced diagnostic data, helping technicians address issues before productivity suffers.
- Stable performance: Reliable communication fosters smoother operations, reducing unplanned stops and manual interventions.
- Future expansion: Systems that allow protocol extensions can accommodate new features without replacing existing hardware.
- Time-saving maintenance: A single communication standard may reduce troubleshooting complexity when handling multiple devices.
Technical managers and design teams often aim to maximize returns on automation investments, and communication standards play a major role in that process. PLCs remain important for monitoring industrial tasks, but they require the right framework for data exchange to deliver consistent results. Looking at serial, Ethernet-based, fieldbus, and wireless solutions can reveal innovative avenues to modernize operations. Cost savings, stakeholder confidence, and flexible design paths often follow once communication systems align with project objectives and process needs.
Engineers across multiple sectors rely on real-time simulation to refine communication strategies, reduce risk, and open new frontiers. OPAL-RT provides decades of experience and an unwavering commitment to innovation, delivering open, scalable, and high-performance platforms. From Hardware-in-the-Loop testing to AI-ready cloud simulation, each solution is designed to help you design, test, and iterate with confidence. Discover how OPAL-RT can support your vision for real-time progress.
Frequently Asked Questions
Why would a project use serial communication instead of an Ethernet-based standard? Some industrial setups rely on older controllers or require minimal wiring, which can make serial methods more appropriate. These types of PLC communication protocols can be cost-effective and straightforward for smaller installations, especially if high-speed data transfer is not a priority. How do you decide between fieldbus networks and Ethernet-based solutions for large-scale automation? Fieldbus often handles specialized tasks with established frameworks like Profibus or DeviceNet, whereas Ethernet-based protocols provide faster communication and simpler integration with modern infrastructure. The selection usually depends on performance goals, investment limitations, and the existing mix of devices. Are wireless PLC communication protocols secure enough for critical processes? Wireless standards have advanced to include robust encryption and secure authentication, reducing the chance of unauthorized access. Engineers generally combine physical network safeguards with strong encryption to maintain data integrity across these types of communication protocols in PLC systems. What factors influence protocol speed when working with different types of communication protocols in PLC? Network topology, cable quality, and device compatibility all play a role in determining how quickly data is exchanged. Certain protocols prioritize deterministic performance, which can be vital for precise control of motor drives and machine components. How does protocol selection contribute to cost savings and faster returns for automation projects? Choosing the right standard can eliminate unnecessary hardware, reduce complexity, and improve real-time feedback, which optimizes overall cycle times. This often translates into fewer production errors, shorter development schedules, and quicker paths to higher returns.